
Secure Software Development: A Security Programmer's Guide: 9781418065478: Computer Science Books @ Amazon.com

Amazon.com : PawHut 3-Tier Wooden Hamster Cage Mice and Rat Cage Small Animals Hutch with Openable Top, Front Door, Storage Shelf : Pet Supplies

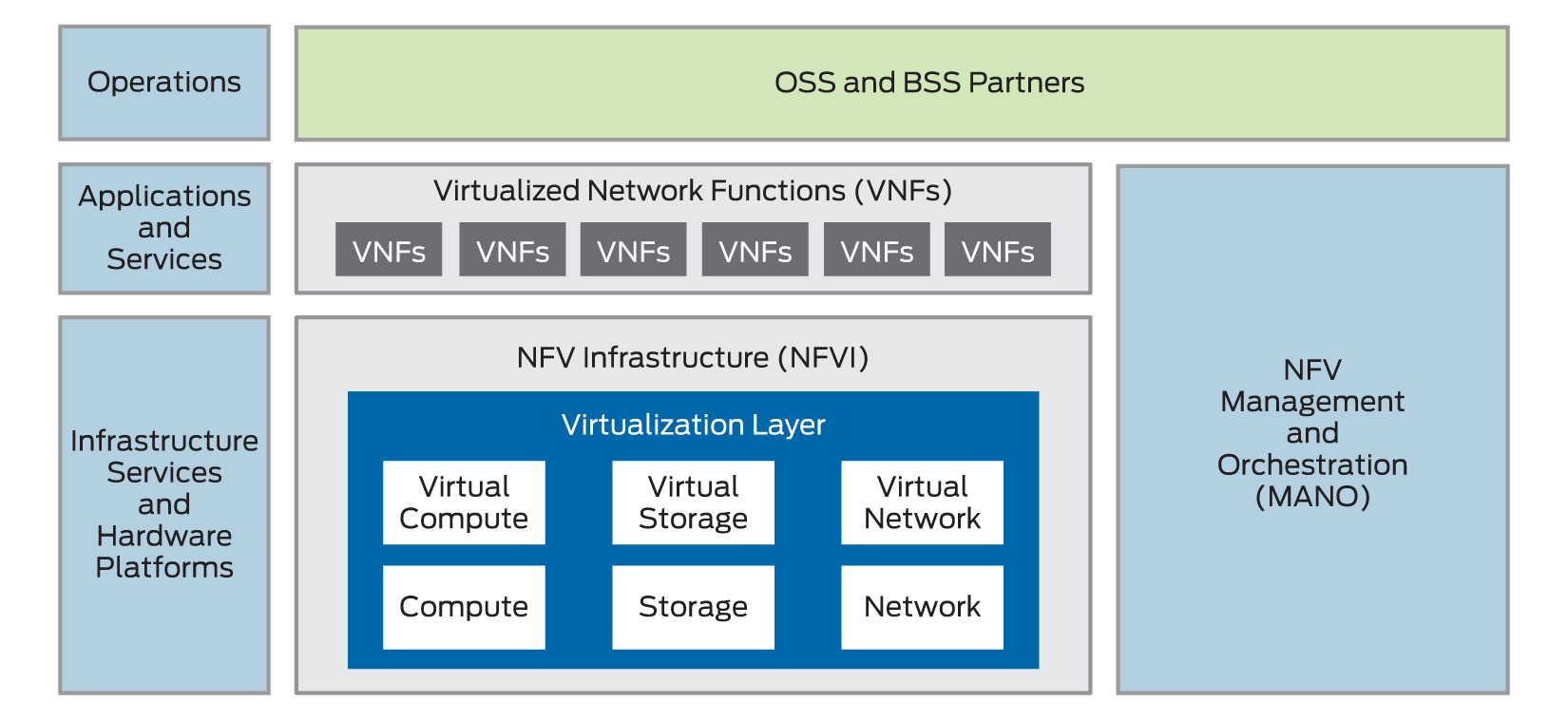
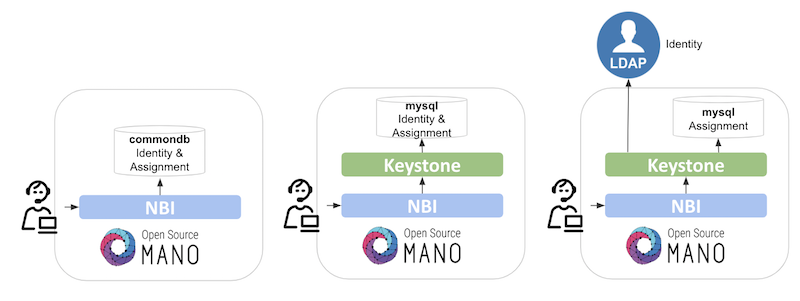
Mapping ETSI MANO to Kubernetes - ETSI NFVO Compliant Orchestration in the Kubernetes/Cloud Native World

OSM - OpenSourceMANO on Twitter: "@ctranoris kicks off 3rd @OpenSourceMANO symposium “#5G Vertical Services” with an all star🌟💫line up of #OSM research projects. @5GinFIRE https://t.co/V1FUYYMdqm" / Twitter

Security in the billions: Toward a multinational strategy to better secure the IoT ecosystem - Atlantic Council














![Document - R4V Southern Cone SitRep - June 2020 [EN] Document - R4V Southern Cone SitRep - June 2020 [EN]](https://data.unhcr.org/images/documents/big_9c451a7e00898a5ff5ec87407e1715177f9040bc.jpg)





